Uncategorized
BlackBerry Report Surfaces Increasing Rate of Cyberattacks
A threat intelligence report published by BlackBerry found that from December 2022 through February 2023, 12 cyberattacks per minute were...
How to deploy DAST to manage AI risks
The use of AI to assist in software development introduces new risks into application security. Here's how to use AppSec...
AutoCrypt KEY provides the key management features needed for automotive production
AutoCrypt KEY enables OEMs and suppliers to manage all types of cryptographic keys used for the components of connected and...
New Android Trojans Infected Many Devices in Asia via Google Play, Phishing
The recently identified Fleckpe Android trojan has infected over 600,000 users in Southeast Asia via Google Play. The post New...
‘Role Is Mostly Symbolic’, Says ENS Director Candidate Ahead of Elections
Anyone could nominate themselves to be an ENS Foundation director but only two stepped forward. Why is that?
New Android Malware ‘FluHorse’ Targeting East Asian Markets with Deceptive Tactics
Various sectors in East Asian markets have been subjected to a new email phishing campaign that distributes a previously undocumented...
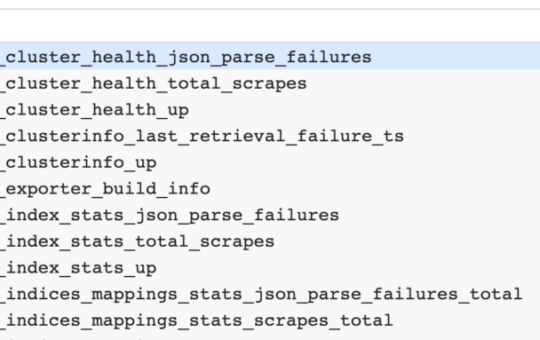
Top metrics for Elasticsearch monitoring with Prometheus
Starting the journey for Elasticsearch monitoring is crucial to get the right visibility and transparency over its behavior. Elasticsearch is...
Binance Lists PEPE as Meme Coin Market Cap Hits $1 Billion
The newly-launched meme coin PEPE has been given another boost after the market's largest exchange, Binance, listed the token this...
Meme Coin Mania: What’s Going On and What Are the Risks?
The roller coaster ride is a compelling draw, but it's rife with risk.