Blog
Over 100,000 Stolen ChatGPT Account Credentials Sold on Dark Web Marketplaces
Over 100,000 compromised OpenAI ChatGPT account credentials have found their way on illicit dark web marketplaces between June 2022 and...
Malicious Code Can Be Anywhere, (Tue, Jun 20th)
My Python hunting rules reported some interesting/suspicious files. The files are named with a “.ma” extension. Some of them have...
Reversing Flutter apps: Dart’s Small Integers
This article delves into the reverse engineering of Dart executable or Flutter release applications. We focus on the reverse engineering...
NDIS agency scrambles over risk of leaked sensitive client information in HWL Ebsworth hack
National Disability Insurance Agency seeking information after 1.1TB of law firm’s data was posted to dark web this month Follow...
UK set to ramp up citizen surveillance program
As part of the 2016 Investigatory Powers Act (IPA), the British government gave several new powers to law enforcement and...
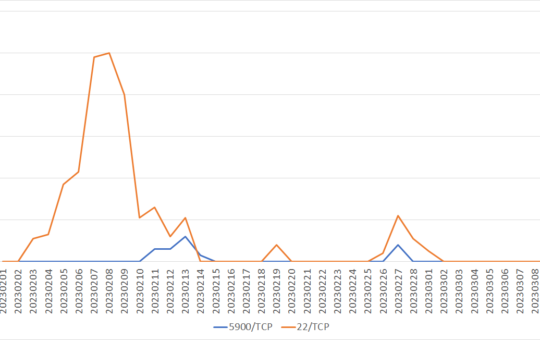
TSUBAME Report Overflow (Jan-Mar 2023)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring...
Hackers Are Actively Using New Mystic Stealer Malware in Cyber Attacks
Recently, the cybersecurity researchers at CYFIRMA found that hackers are actively using “Mystic Stealer Malware,” a new information stealer. It’s...
Hacktivist group Anonymous Sudan a ‘bear in wolf’s clothing’
Researchers say the DDoS focused threat actor is a well-resourced smokescreen for Russian interests. Article Link: Hacktivist group Anonymous Sudan...
Rogue Android Apps Target Pakistani Individuals in Sophisticated Espionage Campaign
Individuals in the Pakistan region have been targeted using two rogue Android apps available on the Google Play Store as...