TSUBAME Report Overflow (Jan-Mar 2023)
This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include. This article covers the monitoring results for the period of January to March 2023. The scan trends observed with TSUBAME sensors in Japan are presented in graphs here.
Observation of suspicious packets sent from a hosting company in Japan
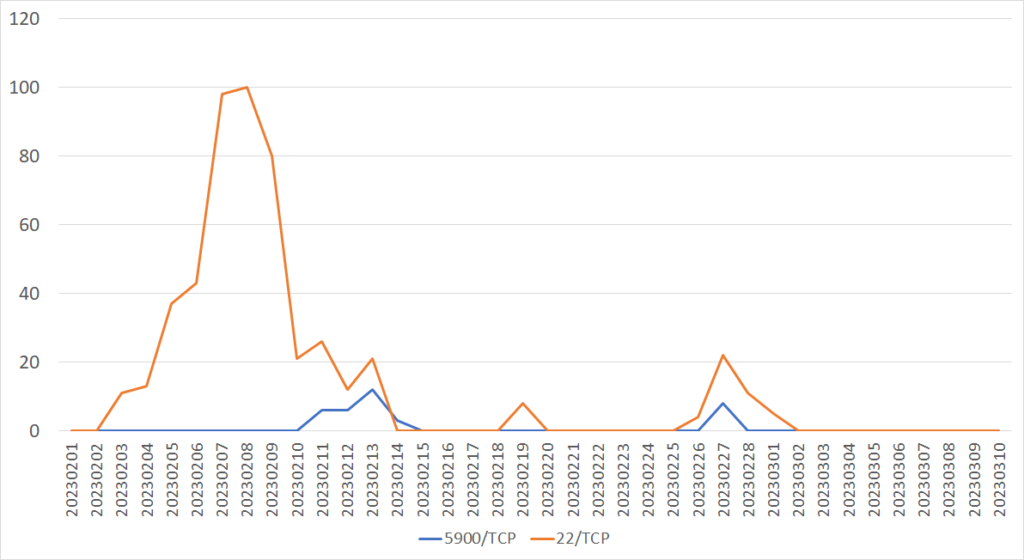
From February to March, we observed a sharp increase in packets sent to Port22/TCP (ssh) and Port5900/TCP (vnc) from multiple IP addresses assigned to organizations in Japan. Figure 1 shows a graph of the number of source hosts per day for 22/TCP and 5900/TCP. Packets sent to 22/TCP were observed from around February 3, with the largest number observed on February 8. Packets sent to 5900/TCP were also observed after February 10. JPCERT/CC provided observation data to the organization several times during the above period so that it would help investigation and response. The number of characteristic packets gradually decreased thanks to the organization’s response, and I believe that the data we provided has contributed to this improvement.
The observed packet trends shown in Figure 1 have several characteristics in addition to the scan packets sent to 5900/TCP since February 10. The suspicious packets were observed from February 10 to 13, February 18 to 19, and February 25 to March 2, and it suggests that scanning activities are conducted mainly on weekends and at the end of the month. We speculate that this series of activity is intended to avoid monitoring.
Figure 1: Trends of suspicious packets sent from a hosting company in Japan
The following part briefly show how I, an analyst of TSUBAME, analyzed the observation data at that time. I would appreciate your comments on it since usually such analysis is not covered in the Internet Threat Monitoring Quarterly Reports.
The source IP addresses that TSUBAME observed may be spoofed. In this data, we focused on the TTL values obtained from the observation to investigate whether they are spoofed or not. There are TSUBAME sensors in multiple regions. The more routers packets go through, the smaller the TTL value will be. Therefore, for packets truly sent from Japan, the TTL values should be smaller in overseas sensors than those in Japan. Table 1 summarizes the TTL values for each sensor. 310 IP addresses were observed this time.
[Table 1: TTL values of observed packets by region]
TTL value
Sensor region
243 ~ 249
JP
234 ~ 238
AU
240 ~ 243
BN
235 ~ 239
GH
235 ~ 239
HK
235 ~ 236
KR
237 ~ 241
LK
230 ~ 233
MA
244 ~ 246
MY
232 ~ 242
TW
Since the sensor in Japan observed higher TTL values, it is likely that the packets were truly sent from the Japanese network. In other words, the attacker is probably either using the resources of a Japanese hosting company as a stepping stone or levaraging it as a legitimate user to conduct the scan activity. JPCERT/CC contacted the company and provided the data to assist its countermeasures.
Comparison of the observation trends in Japan and overseas
Figures 2 and 3 show a monthly comparison of the average number of packets received per day by each sensor in Japan and overseas. More packets were observed by overseas sensors than those in Japan.
Figure 2: Average number of packets to domestic sensors
Figure 3: Average number of packets to overseas sensors
Comparison of monitoring trends by sensor
A global IP address is assigned to each TSUBAME sensor. Table 2 shows the top 10 ports of each sensor which received packets the most. Although the order is different in each sensor, almost all the sensors observed the packets for 23/TCP, 6379/TCP, 22/TCP, and 80/TCP. This suggests that these protocols are being scanned in a wide range of networks.
Table 2: Comparison of top 10 packets by domestic and overseas sensors
#1
#2
#3
#4
#5
#6
#7
#8
#9
#10
Domestic sensor 1
23/TCP
ICMP
22/TCP
123/UDP
6379/TCP
8090/TCP
80/TCP
8088/TCP
445/TCP
3389/TCP
Domestic sensor 2
23/TCP
6379/TCP
ICMP
22/TCP
80/TCP
445/TCP
5555/TCP
3389/TCP
8080/TCP
443/TCP
Domestic sensor 3
23/TCP
6379/TCP
22/TCP
80/TCP
81/TCP
5555/TCP
445/TCP
3389/TCP
8080/TCP
443/TCP
Overseas sensor 1
37215/TCP
23/TCP
22/TCP
52869/TCP
80/TCP
445/TCP
5555/TCP
5060/UDP
3389/TCP
ICMP
Overseas sensor 2
23/TCP
6379/TCP
22/TCP
80/TCP
5555/TCP
ICMP
3389/TCP
443/TCP
1433/TCP
8080/TCP
Overseas sensor 3
23/TCP
445/TCP
6379/TCP
123/UDP
22/TCP
139/TCP
80/TCP
5555/TCP
3389/TCP
ICMP
In closing
Monitoring at multiple points makes it possible to see whether some trends are unique to a particular network. Although we have not published any special alerts as an extra issue or other information this quarter, it is important to pay attention to scanners. We will continue to publish blog articles as the Internet Threat Monitoring Quarterly Report becomes available every quarter. We will also publish an extra issue when we observe any unusual change. Your feedback on this series is much appreciated. Please use the below comment form to let us know which topic you would like us to introduce or discuss further. Thank you for reading.
Keisuke Shikano
(Translated by Takumi Nakano)
Article Link: https://blogs.jpcert.or.jp/en/2023/06/tsubame_overflow_2023-01-03.html
1 post – 1 participant


