Malware Being Distributed Disguised as a Job Application Letter
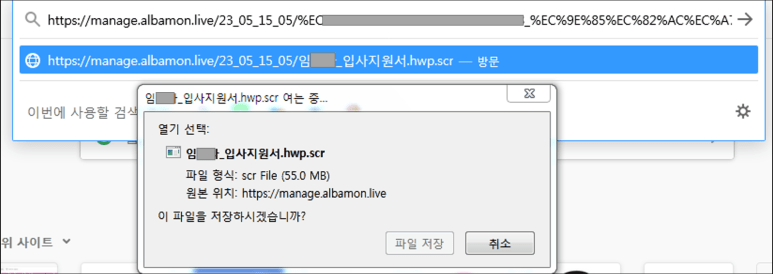
AhnLab Security Emergency response Center (ASEC) has identified that malware disguised as a job application letter is continuously being distributed. This malware is equipped with a feature that checks for the presence of various antivirus processes including a process with AhnLab’s product name (V3Lite.exe) and is being distributed through malicious URLs designed to resemble a Korean job-seeking website. Below are the discovered download URLs.
hxxps://manage.albamon[.]info/download/20230201good001/%EC<omitted>_%EC%9E%85%EC%82%AC%EC%A7%80%EC%9B%90%EC%84%9C.hwp.scr
hxxps://manage.albamon[.]live/23_05_15_05/%EC%<omitted>_%EC%9E%85%EC%82%AC%EC%A7%80%EC%9B%90%EC%84%9C.hwp.scr
hxxps://manage.albamon[.]live/23_05_22_Fighting_ok/%EC<omitted>_%EC%9E%85%EC%82%AC%EC%A7%80%EC%9B%90%EC%84%9C.hwp.scr
The malicious file downloaded from the above URLs has a screen saver file extension (.scr) and an HWP document icon. Upon execution, the compressed file data stored in the internal RCDATA is saved as %Public%[6 ransom characters].zip as shown in Figure 3.
Afterward, it creates additional files by decompressing the above file in the %Public%DocumentsDefender[six random characters] directory. For wechatweb.exe, the created file name consists of six random characters. The files created are shown below.
File Name
Feature
lim_b_n.hwp
Normal HWP file
cmcs21.dll
Decodes and executes yga.txt
wechatweb.exe ([six random characters].exe)
Loads cmcs21.dll
yga.txt
Encoded malicious data
Table 1. Features of each file
It then creates the %Public%Music[six random characters] folder before creating an InternetShortcut file to enable the execution of the normal HWP file created before and wechatweb.exe ([six random characters].exe). This shortcut file is deleted after it is executed.
The HWP document executed via the shortcut file in Figure 6 is a normal document that has the format of a job application letter as shown below.
wechatweb.exe ([six random characters].exe) executed via the shortcut file in Figure 7 loads cmcs21.dll which was created simultaneously and executes the exports function named CMGetCommandString. The loaded cmcs21.dll file registers the following registry entry to enable the malicious file to run continuously.
HKCUSoftwareMicrosoftWindowsCurrentVersionRunspecialyouttg0a
Data: C:UsersPublicDocumentsDefender[six random characters][six random characters].exe(wechatweb.exe)
Afterward, it reads and decodes yga.txt and injects the data into the recursively executed wechatweb.exe ([six random characters].exe) process, ultimately executing malicious behaviors such as information theft. The injected process creates a file named [six random characters].Kinf in the same folder where it encodes and saves keylogging data later on.
It also collects information on various antivirus programs including a process name deemed to be AhnLab’s antivirus software (V3Lite.exe). When certain processes are identified, it sends the information on the right-hand side of Table 2 below, instead of the process name.
Process Name
Transmitted Information
V3Lite.exe
V3
AvastSvc.exe
Avast
NCleanService.exe
NaverCleaner
Nsvmon.npc
NaverVaccine
360rps.exe
360
ZhuDongFangYu.exe
360
AYRTSrv.aye
Naver-NST.exe
KAVsvc.exe
Mcshield.exe
Rising.exe
–
Table 2. Checked process names and transmitted information
Below is a list of other information collected.
0$*[ Drive volume serial number ]$*0515$*$*[ Local PC’s IP information ]$*$*[ PC name ] $* [Username] $* [ OS version information ] $* [ Memory usage ] MB $* [ Processor information ] $* [ Screen resolution] $*$*$* [ Process time information ] $*[ Random value ] $* [ Text in the foreground window ] $* [ Types of antivirus processes in use ] $*2560230837$*zxcv12321$*1111111$*Collected information
This malware can not only collect information but perform a variety of malicious behaviors according to the threat actor’s commands including Internet options configuration, capturing screenshots, managing services, and checking Internet cookie data.
C2 : ggt-send-6187.orange-app[.]vip:6187
Files disguised as Job Application Letter.scr have been continuously distributed as shown below. The recent download URLs for the malware are designed to resemble a Korean job-seeking and recruitment website, and it is difficult for users to recognize that they are fake. Thus, particular caution is advised on the part of users.
Date of Identification
File Name
Feb. 18, 2021
Bae**_Job Application Letter.scr
May 10, 2021
Lee**_Job Application Letter.scr
Jan. 17, 2022
Song**_Job Application Letter.scr
Apr. 04, 2022
Lee**_Job Application Letter.scr
Jan. 31, 2023
Lee**_Job Application Letter.hwp.scr
May 15, 2023
Lim**_Job Application Letter.hwp.scr
Table 3. Additionally identified files
[File Detection]
Dropper/Win.Agent.C5433106 (2023.05.26.02)
Dropper/Win.Agent.C5433107 (2023.05.26.02)
Data/BIN.Encoded (2023.06.01.03)
Trojan/Win32.Agent.C174738 (2016.02.19.09)
[IOC]
MD5
15a0e9cd449bce9e37bb1f8693b3c4e0 (scr)
498eda85200257a813dc6731d3324eb6 (scr)
0ddcb876007aee40f0c819ae2381d1b1 (yga.txt)
ccf3fcd6323bcdd09630e69d6ee74197 (yga.txt)
URL & C2
hxxp://ggt-send-6187.orange-app[.]vip:6187
hxxps://manage.albamon[.]info
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Malware Being Distributed Disguised as a Job Application Letter appeared first on ASEC BLOG.
Article Link: Malware Being Distributed Disguised as a Job Application Letter – ASEC BLOG
1 post – 1 participant


