Tested Techniques for Preventing Cloud Attacks on Your System
<div>
<div>
<div><p>Whenever we see a technology rising in the market, it quickly becomes one of the targets for hackers. The same is happening with the cloud. According to <a href=”https://www.statista.com/statistics/1062879/worldwide-cloud-storage-of-corporate-data/” rel=”noreferrer” target=”_blank”>Statista</a>, as of 2023, 60% of corporate data is stored in a public cloud hosted by AWS, Microsoft, Google, and others.</p>
Additionally, the Compound Annual Growth Rate (CAGR) estimated the growth of cloud will rise from $445.3 billion in 2021 to $947.3 billion by 2026. This means more data will be stored and processed in the cloud and more cloud attacks will occur.
In July 2023, Chinese hackers attacked Microsoft’s cloud (Azure) and stole over 60,000 emails from the U.S. government. This was a cloud attack, and is just one example, numerous others exist.
This article is about cloud computing cyber-attacks, how to prevent them, and how the Hornetsecurity security portfolio helps you achieve cloud security and safety.
</div><div>
<div>
<div>
<div><h2>Cloud Attack: Definition and Causes</h2></div>
</div><div>
<div><p>Cloud attacks, like any other attack is driven by criminals or black hat groups. They exploit vulnerabilities in the cloud systems and inject <a href=”https://www.hornetsecurity.com/en/knowledge-base/malware” rel=”noreferrer” target=”_blank”>malware</a> or they get into the systems such as EC2 instances and then install malicious software. <a href=”https://www.hornetsecurity.com/en/security-information/malware-vs-viruses/” rel=”noreferrer” target=”_blank”>Malware or malicious code</a> stops the system and data from operating and causes business disruption.</p>
How does this happen? There are many different reasons from poor security hygiene to misconfiguration. We will explore it more thoroughly in the next section.
</div><div>
<div>
<div>
<div><h2>Most Common Types of Cloud Computing Attacks</h2></div>
</div><div>
<div><p>Cloud security is a shared responsibility. Just because data is stored within a cloud service, does not mean the cloud provider is liable for the safety of that data. On the contrary, cloud security is a shared responsibility.</p>
According to a Ransomware attacks survey we conducted in 2020, where we asked IT professionals if they believed that data stored within Microsoft 365 was suspectable to ransomware threats, 25% of IT professionals either didn’t know or believed the answer was no. This false belief could lead to various problems, from misconfigurations to security issues.
</div><div>
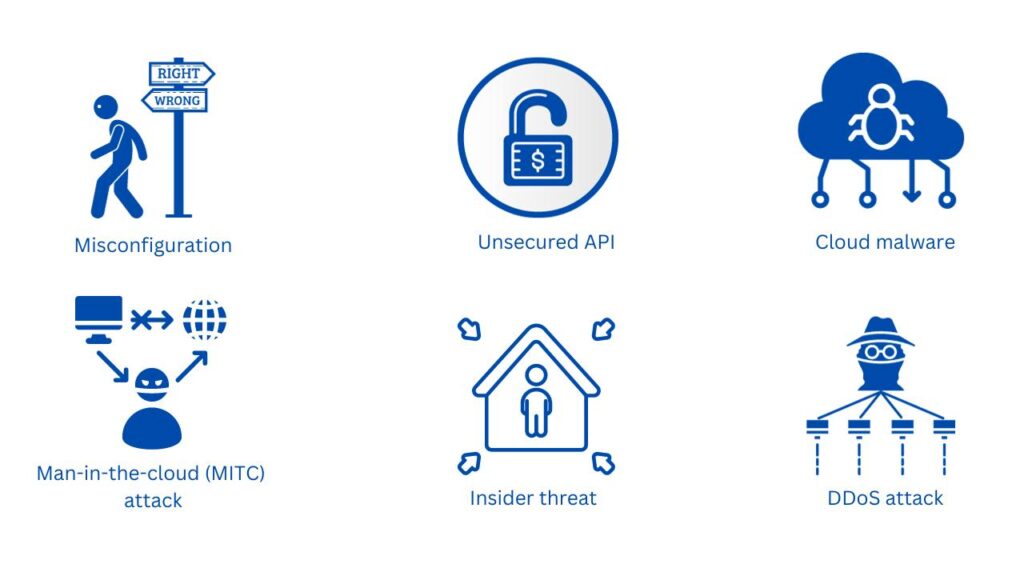
<div><p><strong>Misconfiguration</strong> is one of the main reasons cloud systems or services are compromised by malicious people.</p>
Misconfiguration happens because individuals or teams do not follow security best practices which can lead to several problems such as supply chain attacks, Denial of Service (DoS), Distributed Denial of Service (DDoS), ransomware cloud attacks, and other threats that target Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS).
What can be considered misconfigurations?
It includes poor password policies, lack of 2FA, exposed unused ports, lack of data and database encryption, unsecured APIs, lack of monitoring and logging, publicly accessible storage buckets, mis-configured firewall policies, and others.
Unsecured API falls into the scope of misconfiguration. It is one of the growing risks for an organization that runs or offers cloud services. Some of the known issues are broken user authentication, improper asset management, excessive data exposure, mass injection, lack of resource rate limiting, and more. Unsecured APIs can expose sensitive data and offer unauthorized access to attackers.
Have you heard of a Man-in-the-cloud (MITC) attack? This is a new type of cloud attack that enables an attacker to take control of the victim’s machine via a synchronization account used for OneDrive, Google Drive, Dropbox, and Box. It is called a Man-in-the-cloud attack because the attacker inserts himself between the user and the cloud service and manipulates data between them. How does it happen? Weak credentials.
Have you heard the story of Paige Thompson? She resigned from Amazon, breached firewall vulnerability, and expose publicly the credit information of Capital One’s customers. Paige was an insider threat to the organization.
One of the biggest DDoS (Distributed Denial-of-Service) cloud attacks that reached a size of 2.54 Tbps was done against Google cloud services. An attacker sent spoofed packets to 180,000 servers which forwarded responses to Google servers. Google said they mitigated it.
There are different types of DoS and DDoS cloud attacks, attaching your application, website, hypervisor, and network. Nonetheless, the solution guides us toward the same path. We should implement proper DoS and DDoS protection against website, application, or network attacks.
Hypervisors running in the cloud are also prone to cloud computing cyber-attacks such as VM escape (compromising a VM and then gaining access to the underlying host, and all other VMs on that host), hyperjacking, hypercall, and DoS (Denial-of-Service) attacks, and others.
Hyperjacking is a type of cloud attack in which the attacker takes control of the hypervisor and virtual machines. On the other hand, a hypercall attack is an attack in which the attacker impersonates a guest through the hypercall interface positioned between the domain and hypervisor, subsequently gaining access to the machines.
Cloud malware attacks are one of the most common cloud attacks that happen on-premises and cloud. Attackers are using phishing emails to trick users into executing malicious software that gives them unauthorized access to SaaS, PaaS, or IaaS. One wrong click and your data hosted in the cloud can be infected by ransomware.
</div><div>
<div><p>There are numerous additional types of cloud attacks; however, they are variations on the ones we previously mentioned.</p>
Let’s now investigate some examples of cloud cyber-attacks that occurred in the last decade.
</div><div>
<div>
<div>
<div><h2>Real-World Cloud Attack Examples</h2></div>
</div><div>
<div><p>Numerous cloud cyber-attacks occurred over the last decade. We already mentioned one that happened with Microsoft public cloud in July 2023 and we already mentioned Paige Thompson’s attack in the last section.</p>
She was a former Amazon engineer who resigned, and then exploited a vulnerability in the web application firewall and breached the credit information of Capital One’s customers. Paige exposed credit cards and credit scores, payment history, contact information, and over 100,000 Social Security Numbers.
According to the Department of Justice, Thompson built a tool she used to scan misconfigured accounts in AWS. She was found guilty.
This was considered one of the largest financial data breaches.
In 2020, MongoDB cloud servers were affected by a ransomware attack designed to wipe all data from misconfigured databases. The attacker used a script to find databases which lacked password protection, then deleted the content and uploaded a ransom note demanding payment via Bitcoin.
The hacker also threatened he would report the breach to the General Data Protection Regulation (GDPR) if the victim did not make a payment.
This attack affected almost 23,000 MongoDB databases.
Another misconfigured AWS cloud service, the Amazon S3 (Simple Storage Services) bucket, led to the breach of nearly 200 million U.S. voters. The same company that discovered the exploit, UpGuard, also discovered another one affecting the breach of 6 million Verizon customers. The root cause was the same; misconfigured AWS S3 bucket.
Furthermore, a group of security researchers discovered vulnerabilities with Elasticsearch and Elastic Cloud Enterprise. The vulnerability existed due to not properly controlling the consumption of internal resources. A remote attacker could send a specially crafted HTTP request that causes an OutofMemory error and thus perform a denial of service (Dos) attack.
In recent years, major cloud providers such as Google and AWS experienced DDoS attacks in 2020, GitHub in 2017, and Cloudflare in 2014, among others. Some of them were mitigated due to implemented DDoS protection.
The last one I would like to mention here is the WannaCry ransomware that occurred in 2017. It targeted on-premises Windows machines, but also Windows machines hosted in the cloud. When WannaCry got into Windows, it encrypted data and demanded payment to decrypt them.
As you can gather from these examples, the lack of poor security and misconfiguration leads to breaches.
</div><div>
<div>
<div>
<div><h2>Security Strategies for Protecting Against Cloud Malware</h2></div>
</div><div>
<div><p>There are several security measures you can use in your organization to avoid cloud cyber-attacks. They all fall into strong <a href=”https://www.hornetsecurity.com/en/knowledge-base/it-security/” rel=”noreferrer” target=”_blank”>IT Security</a>.</p></div>
</div><div>
<img alt=”Security Strategies for Protecting Against Cloud Malware” height=”720″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/12/Security-Strategies-for-Protecting-Against-Cloud-Malware.jpg” title=”Security Strategies for Protecting Against Cloud Malware” width=”1280″ />
</div><div>
<div><p><strong>Use strong passwords, and 2FA (two-factor authentication)</strong>. If you are an IT Admin you should enforce password policies such as password strength, password history, frequency of password reuse, password age, and others. On top of that, you should implement two-factor authentication and password-less authentication.</p>
Keep your cloud systems patched. Public cloud providers such as AWS, Microsoft, and Google provide you with virtual machines or databases, however, it is your responsibility to keep them fully patched along with installed software. You can implement centralized update and reporting solutions that do it for you.
We highly recommend you take a backup of your machines, data, and databases. Ensure that your files are backed in different locations and that are protected from ransomware. Hornesecurity’s VM backup supports immutable backup which prevents ransomware or any other malware from making any changes to backup files. Read more in The Backup Bible.
Disable unused ports and protocols. If you are running an EC2 instance, web application, or other cloud service, and you don’t need certain protocols, such as SSH, or RDP, disable them. Many cloud attacks are being carried out through protocols that weren’t even in use.
According to a Palo Alto security report released in 2020, 43% of public cloud databases were unencrypted. These databases are potential attack vendors along with their data. Ensure your databases and data are encrypted, and make sure to implement good key management so that potential attackers can’t access the keys.
Monitoring and logging help you to stay proactive and detect potential issues before they become critical problems for your business. Implementing proper NMS (Network monitoring solution) and SIEM (Security information and event management) is a must-have.
Use secured API. You should ensure that your developers follow security practices when developing API and that they rely on a standard API framework designed with security in mind.
Implement security protection such as Cloud Access Security Broker (CASB), DAM (Database Activity Monitoring), FAM (File Access Monitoring), DLP (Data Loss Prevention), and others.
Perform penetration testing and vulnerability analysis of your cloud services or applications. This helps you to be proactive and strengthen your cloud security.
Educating employees is one of the most important preventive measures you can take. It starts at the IT level and is distributed to developers, pre-sales, technical support, and any users who might have access to your infrastructure. Employees should be educated about IT security, phishing cloud attacks, scams (e.g. QR code scams), and others.
</div><div>
<div>
<div>
<div><h2>Using Security Platforms like Hornetsecurity to Mitigate Against Cloud Malware</h2></div>
</div><div>
<div><p>Hornetsecurity is an all-in-one protection solution covering security, backup, compliance, and security awareness for your employees.</p>
Hornetsecurity VM Backup is a backup solution that helps you back up your virtual machines and data to a safe location. One of the latest features released in version 9 is immutable backup. An immutable backup adds an extra security layer to your backup copies by preventing ransomware cloud attacks.
VM Backup helps you to back up your data to on-premises and cloud including Amazon S3, Wasabi, and Azure.
</div><div>
<div><p>You can learn more about it and trial it here <a href=”https://www.hornetsecurity.com/en/services/vm-backup/?LP=hornetsecurity-Article-VM-Backup-EN&Cat=Blog&utm_source=hornetsecurity-blog&utm_medium=content&utm_campaign=security-awareness-service&utm_content=Article&utm_contentid=cloud-attacks” rel=”noreferrer” target=”_blank”>VM Backup.</a></p>
We mentioned how important is to educate your employees on the latest cyber threats. We provide you with fully automated spear-phishing simulation and cybersecurity training for employees through our Security Awareness Service. According to the Global Risk Report from 2022, 95% of all cyber security incidents are caused by human error.
Security Awareness Service provides you with intelligent awareness benchmarking that measures employee security awareness. It also helps you to roll out the relevant e-learning content tailored to individual roles and simulate different phishing cloud attacks.
</div><div>
<div><p>We are proud to say that Hornetsecurity’s <a href=”https://www.hornetsecurity.com/en/services/cyber-security-awareness-service/?LP=hornetsecurity-Article-SAS-EN&Cat=Blog&utm_source=hornetsecurity-blog&utm_medium=content&utm_campaign=security-awareness-service&utm_content=Article&utm_contentid=cloud-attacks” rel=”noreferrer” target=”_blank”>Security Awareness Service</a> is an award-winning security service.</p>
If you are using Microsoft 365, then you need additional protection through our 365 Total Protection Compliance & Awareness.
It is the next-generation Microsoft security and compliance management solution that offers email security, backup and recovery, compliance and permission management, security awareness, and AI recipient validation. You can explore our plans here.
Furthermore, we provide you with an in-depth analysis of the Microsoft 365 Threat Landscape in our Cyber Security Report 2024. Also, we recommend you take a closer look at the biggest findings of the report.
</div><div>
<div>
<div><div></div></div><div>
<div><p><em>To properly protect your cyber environment, use Hornetsecurity </em><a href=”https://www.hornetsecurity.com/en/services/advanced-threat-protection/?LP=hornetsecurity-Article-ATP-EN&Cat=Blog&utm_source=hornetsecurity-blog&utm_medium=content&utm_campaign=security-awareness-service&utm_content=Article&utm_contentid=cloud-attacks” rel=”noreferrer” target=”_blank”><em>Advanced Threat Protection</em></a><em>, </em><a href=”https://www.hornetsecurity.com/en/services/cyber-security-awareness-service/?LP=hornetsecurity-Article-SAS-EN&Cat=Blog&utm_source=hornetsecurity-blog&utm_medium=content&utm_campaign=security-awareness-service&utm_content=Article&utm_contentid=cloud-attacks” rel=”noreferrer” target=”_blank”><em>Security Awareness Service</em></a><em>, and </em><a href=”https://www.hornetsecurity.com/en/services/vm-backup/?LP=hornetsecurity-Article-VM-Backup-EN&Cat=Blog&utm_source=hornetsecurity-blog&utm_medium=content&utm_campaign=security-awareness-service&utm_content=Article&utm_contentid=cloud-attacks” rel=”noreferrer” target=”_blank”><em>VM backup</em></a><em> to secure your critical data.</em></p>
We work hard perpetually to give our customers confidence in their Spam & Malware Protection, Email Encryption, and Email Archiving strategies.
To keep up to date with the latest articles and practices, pay a visit to our Hornetsecurity blog now.
</div><div>
<div>
<div>
<div><h2>Conclusion</h2></div>
</div><div>
<div><p>In some ways, securing your cloud workloads is different than securing on-premises infrastructure, particularly as it’s a shared responsibility, but in many ways, the same approaches we use on-premises are applicable to any IT environment.</p>
As you’ve learnt in this article, paying attention to basic security hygiene and fostering a security culture in your organization is a crucial first step.
</div><div>
<div>
<div>
<div><h2>FAQ</h2></div>
</div><div>
<h4>How do I stop cloud attacks?</h4>
<div><p>Cloud attacks can be stopped by implementing preventive security measures, often called cyber security hygiene. That includes using strong authentication, implementing strong access control, encrypting data and databases, patching systems, disabling unused ports, educating employees and others.</p>
On top of that, implementing strong infrastructure security solutions such as firewalls, threat detection and response is must-have.
<div><p>Cloud attacks can be detected using different preventive security tools such as cloud monitoring and logging. There are different types of these tools and all of them aim to help you to identify and notify your Team before a small issue turns into a major incident.</p>
On top of that, you should follow different cybersecurity channels that provide insights into ongoing cybersecurity news.
<div><p>Cloud threat is security risk or vulnerability that can compromise data or services hosted in the cloud. It can be spread via different forms such as malware, ransomware, MITM attacks, DoS and DDoS, unsecured API, insider threats, misconfiguration and lack of cybersecurity awareness.</p></div>
</div><div>
<h4>What are the trends for cloud attacks?</h4>
<div><p>Cloud and cybersecurity challenges are continuously evolving. One of the top trends how attackers get into our systems are via phishing, <a href=”https://www.hornetsecurity.com/en/security-information/types-of-social-engineering-attacks/” rel=”noreferrer” target=”_blank”>social engineering</a>, misconfiguration, API attacks, lack of active and tested backups, and others.</p></div>
</div>
</div>
</div>
</div><p>Der Beitrag <a href=”https://www.hornetsecurity.com/en/security-information/cloud-attacks/” rel=”noreferrer” target=”_blank”>Tested Techniques for Preventing Cloud Attacks on Your System</a> erschien zuerst auf <a href=”https://www.hornetsecurity.com/en/” rel=”noreferrer” target=”_blank”>Hornetsecurity</a>.</p>
Article Link: https://www.hornetsecurity.com/en/security-information/cloud-attacks/
1 post – 1 participant


