Microsoft warns of multi-stage AiTM phishing and BEC attacks
Microsoft researchers warn of banking adversary-in-the-middle (AitM) phishing and BEC attacks targeting banking and financial organizations.
Microsoft discovered multi-stage adversary-in-the-middle (AiTM) phishing and business email compromise (BEC) attacks against banking and financial services organizations.
In AiTM phishing, threat actors set up a proxy server between a target user and the website the user wishes to visit, which is the phishing site under the control of the attackers. The proxy server allows attackers to access the traffic and capture the target’s password and the session cookie.
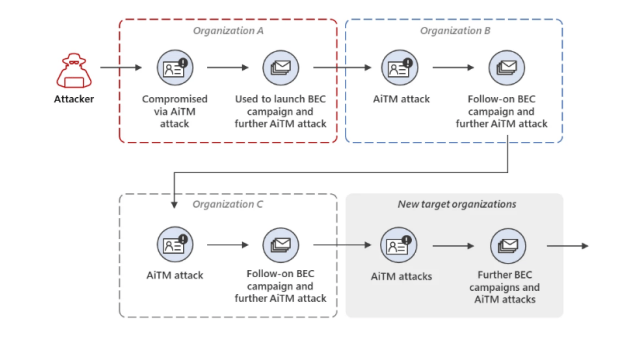
Microsoft discovered that the attackers initially compromised a trusted vendor, then targeted multiple organizations with AiTM attacks and follow-on BEC activities.
“This attack shows the complexity of AiTM and BEC threats, which abuse trusted relationships between vendors, suppliers, and other partner organizations with the intent of financial fraud.” reads the analysis published by Microsoft. “While the attack achieved the end goal of a typical AiTM phishing attack followed by business email compromise, notable aspects, such as the use of indirect proxy rather than the typical reverse proxy techniques, exemplify the continuous evolution of these threats.”
This campaign outstands for the use of an indirect proxy that provided attackers control and flexibility in tailoring the phishing pages to their targets and steal session cookies. Upon signing in with the stolen cookie through a session replay attack, the attackers leveraged multifactor authentication (MFA) policies that have not properly to update MFA methods without an MFA challenge. Then the attacker sent out more than 16,000 emails to the target’s contacts as part of a second-stage phishing campaign.
Microsoft states that affected organizations need to revoke session cookies and roll back modifications made by the threat actor in the MFA process.
Microsoft attributes the attack to an emerging cluster tracked as Storm-1167.
The attack chain starts with a phishing email that includes a link pointing to a fake Microsoft sign-in page. The page is designed to trick visitors into entering their credentials and 2FA code.
Then attackers use the stolen credentials and session cookies to access the victim’s mail inbox through a replay attack. The stolen data are also used to carry out a BEC attack.
Microsoft pointed out that AiTM phishing attack leads to second-stage BEC which was also detailed in the report published by the researchers.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, cyberattack)
The post Microsoft warns of multi-stage AiTM phishing and BEC attacks appeared first on Security Affairs.


