Kimsuky Distributing CHM Malware Under Various Subjects
AhnLab Security Emergency response Center (ASEC) has continuously been tracking the Kimsuky group’s APT attacks. This post will cover the details confirmed during the past month of May. While the Kimsuky group often used document files for malware distribution, there have been many recent cases where CHM files were used in distribution. Also, unlike in the past when the document files contained North Korea-related topics, the group is now attempting to attack using a variety of subjects.
(1) Cases of Distribution
The names of the distributed files found during May are as follows. They show a variety of subjects such as cryptocurrency, tax accounting, and contracts, and it seems the personal data of a certain individual is being used.
File Names Used in Distribution
(Coinone)Client Transaction Confirmation.chm
202305050017 Order Sheet (1).chm
BITWAK Application Form.chm
20230412_Tax Investigation Return Guidelines.chm
2023 Annual Membership Fee Payment-related Materials(****).chm
Revised Lease Contract.chm
Payment Slip.chm
League of Legends Restricted Account Notice (Riot Games).chm
Written Act for the 2023 1st Provisional General Meeting.chm
Tuition Receipt.chm
CTP Lockup Cancellation Notice(***).chm
Materials for Publication Fees for Volume 23 Issue 5(***).chm
Rental(Renewal) Application Materials for Gumi General Business Support Center (***).chm
Listing Deliberation Materials.chm
*** Proof of Social Insurance Subscription.chm
Table 1. File names used in distribution
The CHM malware in distribution generates a normal help window upon execution and performs malicious behaviors through the malicious script inside. It is not easy for users to notice the malicious behaviors, having been deceived with the help window disguised as a normal file. The help window generated in the user’s PC has a different topic according to which particular field the target works in. Below are some of the common examples.
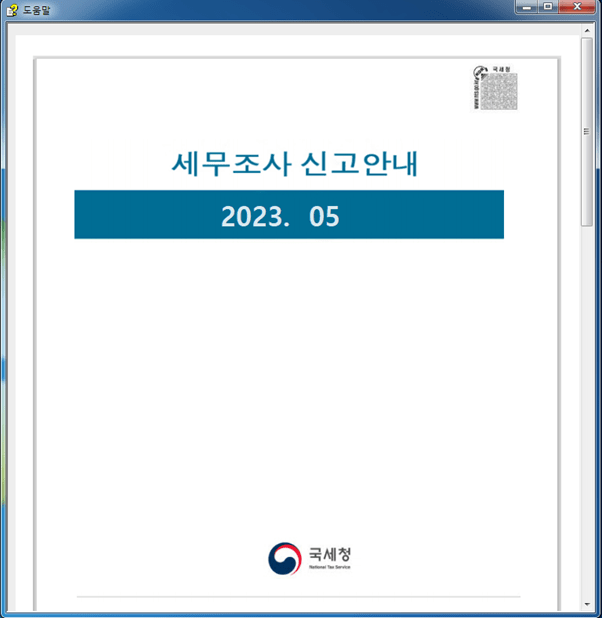
Figure 1 shows the type that was disguised as a National Tax Service tax investigation return guide for users that must file tax returns. The global income tax return season in Korea falls in May, and the threat actor seems to have taken advantage of this fact.
Figure 2 shows the type disguised as financial transaction data between certain users. The actual account number and transaction histories can be seen, and this may have been created using stolen personal data.
Figure 3 shows the type disguised as cryptocurrency transaction data. Like the second case, it contains personal data such as an actual user’s email and phone number.
There are also other types such as contracts, certificates, and order sheets as shown in Figure 4. These are the major files in distribution, but as there are files disguised as the household register of a certain individual, ticket reservation details, and other topics, users are advised to practice particular caution.
(2) Operation Process
The overall operation flow of this CHM type is shown in Figure 5. Additional scripts are downloaded to exfiltrate user information and download additional malware. Each step is outlined below.
The malicious script in the CHM is shown in Figure 6. Malicious commands are executed through a shortcut object, and this object is called through the Click method.
Executed Command
cmd, /c start /MIN REG ADD HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun /v oeirituttvv /t REG_SZ /d “%USERPROFILE%Linksoeirituttvv.vbs” /f & echo [Encoded command] > “%USERPROFILE%Linksoeirituttbb.dat” & echo [Encoded command] > “%USERPROFILE%Linksoeirituttvv.dat” & start /MIN certutil -decode “%USERPROFILE%Linksoeirituttvv.dat” “%USERPROFILE%Linksoeirituttvv.vbs” & start /MIN certutil -decode “%USERPROFILE%Linksoeirituttbb.dat” “%USERPROFILE%Linksoeirituttbb.bat” & start /MIN timeout -t 1 /nobreak & start /MIN CScript “%USERPROFILE%Linksoeirituttvv.vbs” & start /MIN timeout -t 2 /nobreak & start /MIN CScript “%USERPROFILE%Linksoeirituttvv.vbs
This command saves two encoded commands under “%USERPROFILE%Linksoeirituttbb.dat” and “%USERPROFILE%Linksoeirituttvv.dat” and saves the commands decrypted through certutil in the files oeirituttbb.vbs and oeirituttvv.bat. Afterward, it runs oeirituttbb.vbs and registers oeirituttbb.vbs to the RUN key to enable it to run continuously.
Oeirituttbb.vbs is a runner that runs the oeirituttvv.bat file created with it. oeirituttvv.bat downloads additional malicious files through curl. Two files are downloaded: a BAT file and a CAB file.
Download URL
hxxp://vndjgheruewy1[.]com/tnd/pung03.txt
hxxp://vndjgheruewy1[.]com/tnd/qung03.txt
The downloaded BAT file (pung03.bat) decompresses the CAB file (qung03.cab), then runs temprr03.bat. The CAB file contains a total of 6 scripts. The features of each script are outlined in Table 2.
File Name
Feature
temprr03.bat
Runs loyes03.bat
loyes03.bat
Registers to RunKey (mnasrt.vbs)
Runs loyestemp03.bat
Runs dwpp.vbs
mnasrt.vbs
Runs loyes03.bat
loyestemp03.bat
Collects user information
Runs uwpp.vbs
dwpp.vbs
Downloads CAB
uwpp.vbs
Uploads user information
Table 2. Features of each script
The final malicious behaviors performed by this script are exfiltrating user information and downloading additional malicious files.
File Name
Saved Information
cudk.txt
List of files on the Desktop (including subfolders)
ipif.txt
IP information
stif.txt
System information
Table 3. Exfiltrated information
The code for the exfiltration of user information is shown in Figure 9, and the pieces of exfiltrated information are shown in Table 3. User information is collected through loyestemp03.bat, and uwpp.vbs sends the collected information along with the PC name to “hxxp://vndjgheruewy1[.]com/uun06/uwpp.php”.
The code for file download is shown in Figure 10. It seems that the threat actor checks the stolen user information, and only when the system is a target of attack, uploads additional malicious files to the C2. If the system is a target, the threat actor uploads files with the infected PC’s name. Infected PCs continuously make attempts to download through the script registered to RunKey, and when additional files are uploaded, the files are downloaded. It then decompresses the downloaded files through the expand command before executing them. This allows us to assume that the additional file is also a CAB file.
Download URL
hxxp://vndjgheruewy1[.]com/jun06/dw_%COMPUTERNAME%.dat
As such, more elaborate attacks have become possible because the types of malicious files downloaded may differ according to the attack target. Recently, there has been an increase in malware distribution targeting particular users using personal information. Cases of using CHM files in APT attacks are also commonly found. Users must carefully check the senders of emails and refrain from opening files from unknown sources. They should also perform routine PC checks and always keep their security products updated to the latest version.
[File Detection]
Downloader/CHM.Generic (2023.06.03.00)
Trojan/BAT.Runner (2023.06.17.00)
Trojan/VBS.Runner (2023.06.17.00)
Downloader/BAT.Generic (2023.06.17.00)
Downloader/VBS.Generic (2023.06.17.00)
Infostealer/BAT.Generic (2023.06.17.00)
Infostealer/VBS.Generic (2023.06.17.00)
[IOC]
b5a873ee6b839cbd03789115fc3ae944
9861999409cdbc1f7c4c1079d348697c
7c7b8dd6dd4ba7b443e84287671f0e79
98764ae00cee9f2cc87530601c159387
d62dcb76fa0fb4b725ea9c8643874ae7
e9e56ee78e019e09d5dbe0bb373adf09
ef58a1326b98feccc90c4d37a8ce2fe2
ae6fdb8945991b587ab790c2121345ce
075160d6c8d82b96d1ae7893761695a6
e5b0430290dc71193b7ea2fc829a9910
hxxp://vndjgheruewy1[.]com/tnd/pung03.txt
hxxp://vndjgheruewy1[.]com/tnd/qung03.txt
hxxp://vndjgheruewy1[.]com/uun06/uwpp.php
hxxp://vndjgheruewy1[.]com/jun06/dw_%COMPUTERNAME%.dat
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Kimsuky Distributing CHM Malware Under Various Subjects appeared first on ASEC BLOG.
Article Link: https://asec.ahnlab.com/en/54678/
1 post – 1 participant


