Introducing Microsoft 365 Permission Manager – Manage Permissions and Enforce Compliance Effortlessly
<div>
<div>
<div><h2>Introduction</h2></div>
</div><div>
<div><p>There are three pillars of a Zero Trust approach to cyber security:</p>
Verify explicitly
Assume breach
Use least-privilege access
The first one is about verifying every connection (no network connection is safe just because it’s coming from an internal network) and the second one is about segmenting your network so that when a breach occurs it doesn’t automatically mean your entire network is compromised.
But it’s the third one we’re going to look at in this article. It’s been around for a lot longer than the concept of Zero trust, in fact it’s been taught in IT admin 101 classes for several decades. In real life however, it’s incredibly difficult to implement and maintain. For all you IT admins – how do you tell who’s worked the longest at a business by just looking in Active Directory? Simple – just look at the number of groups a user is a member of – more equals longer tenure.
In other words, granting people (and apps, scripts etc.) permissions to get something done is easy, making sure they only have the access they need over time by removing unused permissions is exceedingly hard.
Cloud hasn’t helped much, as we’ve now got interrelated SaaS applications, several cloud storage locations and a more complex web of identity and access governance configuration. Modern ways of working, with a lot of sharing of data with external partners also doesn’t improve the situation. And finally, vendors themselves don’t help much as more sharing and usage of their tools equals more “stickiness” and adoption, so controls to govern security and sharing aren’t intuitive or easy to use (or even find). There’s also an element of users having become comfortable with sharing documents easily, and if your IT security team outright blocks sharing of documents externally from SharePoint and OneDrive for Business for example, they’ll simply use another way (personal email / cloud storage etc. – I’ve even seen Facebook Messenger used). This alternate method is probably completely invisible to your IT Security Team, making the situation even worse.
As a long time IT admin and MSP owner, the recently released 365 Permission Manager from Hornetsecurity is a really interesting and unique tool to tackle this exact problem for your Microsoft 365 business data.
To see more about the overall risk landscape for your business, download our free 2023 Cyber Security Report.
</div><div>
<div>
<div>
<div><h2>Knowing you have a problem is half the battle</h2></div>
</div><div>
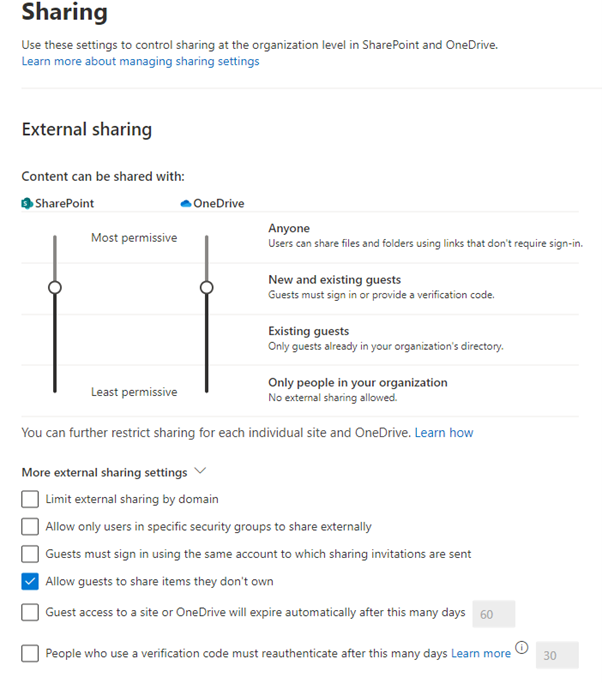
<div><p>Let’s start with a quick recap of the built in sharing settings today for your Microsoft 365 business data. You can allow sharing of documents in a SharePoint site externally anonymously (don’t do that), requiring authentication (creating a new guest user if the account didn’t exist already), only allow sharing with existing guests (they must be invited through another process) or not allowing external sharing at all.</p></div>
</div><div>
<img alt=”Built in document sharing options in M365″ height=”683″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/06/Built-in-document-sharing-options-in-M365.png” title=”Built in document sharing options in M365″ width=”602″ />
</div><div>
<div><p>Then you can further restrict these tenant wide settings on a per site or OneDrive site basis. But there’s no centralized console to monitor these custom permissions, nor a way to create templates to apply the appropriate governance to different sites and most importantly, no easy way to see what’s been shared with whom (internally or externally) or see exactly what an individual user has access to.</p>
All of these missing features are offered in Hornetsecurity 365 Permission Manager which connects to your Microsoft 365 (Azure AD) tenant and is then given permission to query and manage permissions for SharePoint, OneDrive and Teams sites. There’s a set of built in Compliance Policies (and you can create custom ones, see below) that you can set as default for sites.
The dashboard shows you at a glance the proportion of your sites that are compliant with the policy you’ve applied to them, so you get an initial idea of “how bad it is”.
</div><div>
<div><p>Your next stop is Explore Sites module, where you can see every SharePoint site (), Teams site () and OneDrive site () and if they allow anonymous access, organization wide access or external user access.</p></div>
</div><div>
<img alt=”Explore Sites sharing and compliance” height=”395″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/06/Explore-Sites-sharing-and-compliance.png” title=”Explore Sites sharing and compliance” width=”601″ />
</div><div>
<div><p>You can see the policies you’ve applied to each site and whether the site is compliant with it, and the Audit button takes you to a wizard with pages that show you why it’s not. Here you can also remediate Site & Group violation or Item Access Violations by either clicking the Fix button, which will remove or change permissions, or if there’s a genuine business reason for the violation, you can Approve it.</p></div>
</div><div>
<img alt=”Auditing a non-compliant site” height=”308″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/06/Auditing-a-non-compliant-site.png” title=”Auditing a non-compliant site” width=”602″ />
</div><div>
<div><p>Back in the Explore Sites module you can click on the Explore buttons to see individual folders and documents within a site, adjust the permissions, and filter the view based on anonymous links, custom permissions, inherited permissions or being shared with a named external user.</p>
An innocent looking eye button lets you do something very cool, pick an individual user and see content from their point of view. Which SharePoint, Teams and OneDrive sites do they have access to? It’s incredibly powerful to have these exploratory tools in one place and much easier than investigating this using the built in SharePoint / Teams admin tools.
In the Compliance Policies module you can see the four built in policies:
Public (external sharing)
Evergreen (internal sharing only)
Confidential (specific groups / users only)
Sensitive (specific users only, contains sensitive documents)
These can’t be changed but you can copy them as a starting point for a custom policy, or you can create a custom policy from scratch. Essentially all the sharing / permissions related settings in the native tools (that are spread across different screens) are gathered here in one place, and instead of defining a single default for the organization, that you then need to further restrict, you build exactly the policy that matches your business or regulatory governance requirements and apply it to the appropriate sites.
There are two pages in the wizard, the first one covers general internal and external sharing settings.
</div><div>
<div><p>The second page lets you set governance settings such as how often the site should be audited against the policy, how often to send email notifications of violations and if there are any trusted external domains to allow sharing with.</p></div>
</div><div>
<img alt=”Creating a custom compliance policy for sharing – governance settings” height=”281″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/06/Creating-a-custom-compliance-policy-for-sharing-governance-settings.png” title=”Creating a custom compliance policy for sharing – governance settings” width=”602″ />
</div><div>
<div><p>As you can imagine, when you first enable this in a loosely governed tenant, you’re likely to see some really scary sites and settings and this is where the super handy To Do module comes in. Here you can see a list of all policy violations, you can filter by site or violation reason and you can either Fix or Approve each item individually, or simply select all of them (in your filtered list) and apply the action.</p></div>
</div><div>
<img alt=”To do list with Approve or Fix options” height=”275″ src=”https://www.hornetsecurity.com/wp-content/uploads/2023/06/To-do-list-with-Approve-or-Fix-options.png” title=”To do list with Approve or Fix options” width=”601″ />
</div><div>
<div><p>As an IT admin I love tools like this which don’t just present an overwhelming list of stuff for me to do, but a filterable, priority list of items to fix, plus easy ways to do just that.</p>
The overall problem of ungoverned sharing of Microsoft 365 business data in an organization will of course land on the IT departments desk, but it’s a larger issue where you’ll need to involve the rest of the business and decision makers, and they’ll need reports to see the scope of the problem. There are three provided in the Reports module: Full Site Permissions, User & Group Access and External Access. When these are generated they’re password protected so make sure to grab that password so you can access the resulting report.
Finally, as befits a security and governance tool, every administrative action taken in 365 Permission Manager is logged in the Activity Log.
</div><div>
<a href=”https://www.hornetsecurity.com/en/services/365-permission-manager/” rel=”noreferrer” target=”_blank”>Learn more</a>
</div>
</div>
</div><div>
<div>
<div><div></div></div><div>
<div><h2>Frequently Asked Questions</h2></div>
</div><div>
<h5>Why do you need Microsoft 365 Permission Manager?</h5>
<div><p>Managing permissions for your Microsoft 365 business data (SharePoint, Teams and OneDrive) in a tenant is very hard to do at scale. Permissions Manager helps you manage this and to achieve true least privilege access for both internal users and external guests.</p></div>
</div><div>
<h5>What are the benefits of Microsoft 365 Permission Manager?</h5>
<div><p>It lets you see exactly what permissions and sharing is configured across all current SharePoint / Teams and OneDrive sites. Furthermore you can use the built in compliance policies, or customize your own to apply granular permissions templates to different sites, that have different governance needs. You can then fix any policy violations with a simple button click, report on settings to management and continuously monitor new sites and sharing settings.</p></div>
</div><div>
<h5>What are the features of Microsoft 365 Permission Manager?</h5>
<div><p>The Compliance Policies module lets you use built in policies, or create your own, custom templates that you can then apply to different sites that have different sharing needs. The Explore Sites module shows you all sites, whether they’re compliant with the policy you’ve applied and lets you Audit violations and Explore the sharing settings on content. The To Do module presents a filterable list of all violations to make it easy to fix them, and the Reports module gives you emailed reports on the state of permissions across your digital estate.</p></div>
</div><div>
<h5>What is a GRC service?</h5>
<div><p>GRC stands for Governance, Risk and Compliance and 365 Permission Manager is a tool to govern sharing settings and permissions for your Microsoft 365 business data through built in and custom policies, manage risk by applying the principle of Least Privilege to this sharing and reporting on the compliance of the settings by highlighting any violations of your applied policies.</p></div>
</div><div>
<h5>How can I Track a Company’s Compliance in the 365 Permission Manager Dashboard?</h5>
<div><p>The dashboard gives you an “at a glance” view of the percentage of your sites that are compliant with your policies across the three types (SharePoint, Teams and OneDrive) and also tracks the violation trends over time, to give you an indication as to how your remediation efforts are improving your overall GRC stance.</p></div>
</div><div><div></div></div>
</div>
</div><div>
<div>
<div>
<div><h2>Conclusion</h2></div>
</div><div>
<div>365 Permission Manager is a unique solution to a very difficult problem, managing access to your Microsoft 365 business data, one that no amount of end user training (<a href=”https://www.hornetsecurity.com/en/security-information/security-awareness-training/” rel=”noreferrer” target=”_blank”>Security Awareness Training</a>) or written company policy is going to address – users need to share documents internally and externally and it’s very easy to do so with the default settings. Security, risk management and least privilege are afterthoughts in most organization (hence the remarkable risk of <a href=”https://www.hornetsecurity.com/en/knowledge-base/ransomware/ransomware-attacks-survey-2022/” rel=”noreferrer” target=”_blank”>ransomware attacks succeeding</a>) and leads to high levels of risk of data leakage and the built in tools in Microsoft 365 do not adequately address this risk – 365 Permission Manager does. Try it out today!</div>
</div>
</div>
</div>
</div><p>Der Beitrag <a href=”https://www.hornetsecurity.com/en/security-information/manage-permissions-and-enforce-compliance-effortlessly/” rel=”noreferrer” target=”_blank”>Introducing Microsoft 365 Permission Manager – Manage Permissions and Enforce Compliance Effortlessly</a> erschien zuerst auf <a href=”https://www.hornetsecurity.com/en/” rel=”noreferrer” target=”_blank”>Hornetsecurity</a>.</p>
Article Link: https://www.hornetsecurity.com/en/security-information/manage-permissions-and-enforce-compliance-effortlessly/
1 post – 1 participant


