Community Contribution Highlights — SentinelOne Joins PySIGMA
Community Contribution Highlights — SentinelOne Joins PySIGMA
https://github.com/7RedViolin/pySigma-backend-sentinelone
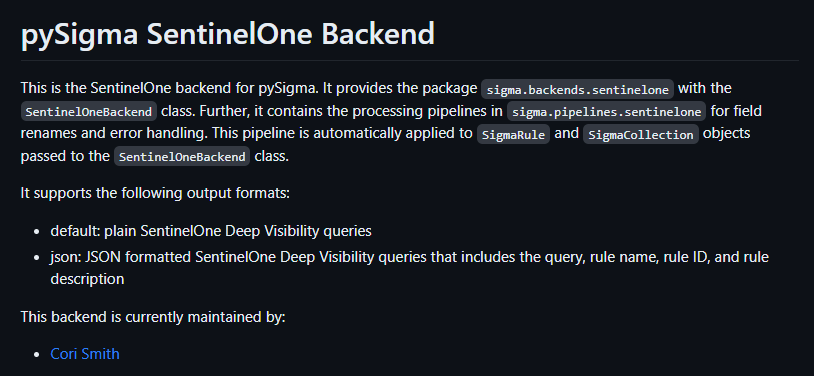
We’re happy to announce a new backend addition to the growing list of PySIGMA supported backends thanks to a community contribution by Cori Smith (7RedViolin)
Using the latest and greatest version of sigma-cli you can immediately make use of this backend and start converting SIGMA rules into SentinelOne Deep Visibility queries.
As an example we’ll take the “Suspicious Microsoft OneNote Child Process” and convert it to a SentinelOne Deep Visibility query.
Snippet from the SIGMA rule
We first check the list of backends available to use via sigma-cli, using the following command: sigma plugin list
Plugin list
Once we identified the backend, we can install it using the command: sigma plugin install sentinelone
We can then start the conversion of the rule with the command shown below.
sigma convert -t sentinelone proc_creation_win_office_onenote_susp_child_processes.yml
EventType = “Process Creation” AND (EndpointOS = “windows” AND (SrcProcName endswithCIS “\onenote.exe” AND (((OriginalFileName In Contains AnyCase (“bitsadmin.exe”,”CertOC.exe”,”CertUtil.exe”,”Cmd.Exe”,”CMSTP.EXE”,”cscript.exe”,”curl.exe”,”HH.exe”,”IEExec.exe”,”InstallUtil.exe”,”javaw.exe”,”Microsoft.Workflow.Compiler.exe”,”msdt.exe”,”MSHTA.EXE”,”msiexec.exe”,”Msxsl.exe”,”odbcconf.exe”,”pcalua.exe”,”PowerShell.EXE”,”RegAsm.exe”,”RegSvcs.exe”,”REGSVR32.exe”,”RUNDLL32.exe”,”schtasks.exe”,”ScriptRunner.exe”,”wmic.exe”,”WorkFolders.exe”,”wscript.exe”)) OR (TgtProcName endswithCIS “\AppVLP.exe” OR TgtProcName endswithCIS “\bash.exe” OR TgtProcName endswithCIS “\bitsadmin.exe” OR TgtProcName endswithCIS “\certoc.exe” OR TgtProcName endswithCIS “\certutil.exe” OR TgtProcName endswithCIS “\cmd.exe” OR TgtProcName endswithCIS “\cmstp.exe” OR TgtProcName endswithCIS “\control.exe” OR TgtProcName endswithCIS “\cscript.exe” OR TgtProcName endswithCIS “\curl.exe” OR TgtProcName endswithCIS “\forfiles.exe” OR TgtProcName endswithCIS “\hh.exe” OR TgtProcName endswithCIS “\ieexec.exe” OR TgtProcName endswithCIS “\installutil.exe” OR TgtProcName endswithCIS “\javaw.exe” OR TgtProcName endswithCIS “\mftrace.exe” OR TgtProcName endswithCIS “\Microsoft.Workflow.Compiler.exe” OR TgtProcName endswithCIS “\msbuild.exe” OR TgtProcName endswithCIS “\msdt.exe” OR TgtProcName endswithCIS “\mshta.exe” OR TgtProcName endswithCIS “\msidb.exe” OR TgtProcName endswithCIS “\msiexec.exe” OR TgtProcName endswithCIS “\msxsl.exe” OR TgtProcName endswithCIS “\odbcconf.exe” OR TgtProcName endswithCIS “\pcalua.exe” OR TgtProcName endswithCIS “\powershell.exe” OR TgtProcName endswithCIS “\pwsh.exe” OR TgtProcName endswithCIS “\regasm.exe” OR TgtProcName endswithCIS “\regsvcs.exe” OR TgtProcName endswithCIS “\regsvr32.exe” OR TgtProcName endswithCIS “\rundll32.exe” OR TgtProcName endswithCIS “\schtasks.exe” OR TgtProcName endswithCIS “\scrcons.exe” OR TgtProcName endswithCIS “\scriptrunner.exe” OR TgtProcName endswithCIS “\sh.exe” OR TgtProcName endswithCIS “\svchost.exe” OR TgtProcName endswithCIS “\verclsid.exe” OR TgtProcName endswithCIS “\wmic.exe” OR TgtProcName endswithCIS “\workfolders.exe” OR TgtProcName endswithCIS “\wscript.exe”)) OR (TgtProcName endswithCIS “\explorer.exe” AND (TgtProcCmdLine containsCIS “.hta” OR TgtProcCmdLine containsCIS “.vb” OR TgtProcCmdLine containsCIS “.wsh” OR TgtProcCmdLine containsCIS “.js” OR TgtProcCmdLine containsCIS “.ps” OR TgtProcCmdLine containsCIS “.scr” OR TgtProcCmdLine containsCIS “.pif” OR TgtProcCmdLine containsCIS “.bat” OR TgtProcCmdLine containsCIS “.cmd”)) OR (TgtProcName containsCIS “\AppData\” OR TgtProcName containsCIS “\Users\Public\” OR TgtProcName containsCIS “\ProgramData\” OR TgtProcName containsCIS “\Windows\Tasks\” OR TgtProcName containsCIS “\Windows\Temp\” OR TgtProcName containsCIS “\Windows\System32\Tasks\”)) AND (NOT ((TgtProcName endswithCIS “\AppData\Local\Microsoft\Teams\current\Teams.exe” AND TgtProcCmdLine endswithCIS “-Embedding”) OR (TgtProcName containsCIS “\AppData\Local\Microsoft\OneDrive\” AND TgtProcName endswithCIS “\FileCoAuth.exe” AND TgtProcCmdLine endswithCIS “-Embedding”)))))
SentinelOne users can directly copy the output and start hunting for some malicious Onenote child processes.
Further Contribution
If you’re interested in building a similar PySIGMA backend you cant get started by checking out the pySigma Cookie Cutter Template
If you want to contribute to the SentinelOne backend you can do so here
Subscribe to Publication
If you’re interested in regular updates on the SIGMA project, please be sure to subscribe to this publication and follow @sigma_hq on Twitter.
Community Contribution Highlights — SentinelOne Joins PySIGMA was originally published in Sigma_HQ on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Community Contribution Highlights — SentinelOne Joins PySIGMA | by Nasreddine Bencherchali | Sigma_HQ | Apr, 2023 | Medium
1 post – 1 participant


